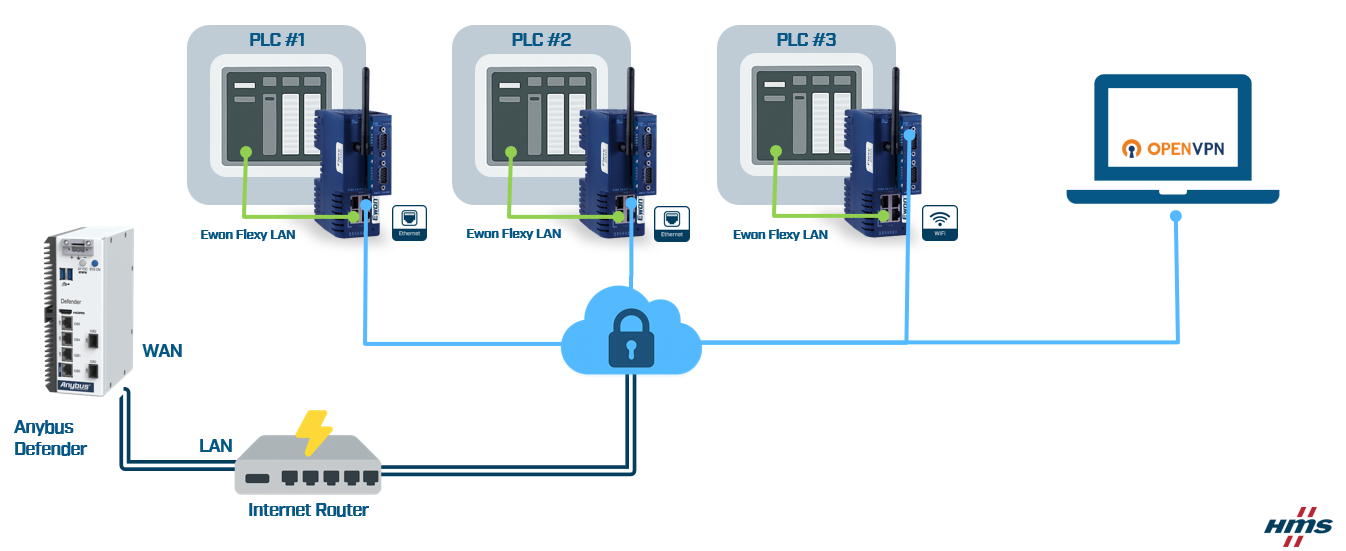
This article describes how to configure the Anybus defender as an OpenVPN server for building your own VPN Network using Ewon Devices and computers.
APPLICABLE PRODUCTS
Anybus Defender 4002, 6004, 6024 DPI/PROFW
Ewon Flexy
Ewon Cosy+
VERSIONS USED IN THIS ARTICLE
- Anybus Defender
- Flexy 205 14.9s4
- Cosy+ 22.0s4
IN THIS ARTICLE
ANYBUS DEFENDER CONFIGURATION
WAN IP Address & Firewall
Begin by assigning an IP address to the WAN interface of your Defender. This IP address must belong to the same subnet as the LAN network of your internet router. In most cases, you will need to set a static IP address manually, although some routers may assign it automatically via DHCP. Regardless of the method, it's crucial that this IP address remains consistent, as it will be referenced in a port forwarding rule on your internet router. This rule is necessary to allow remote access to the Defender's WAN interface from the internet.
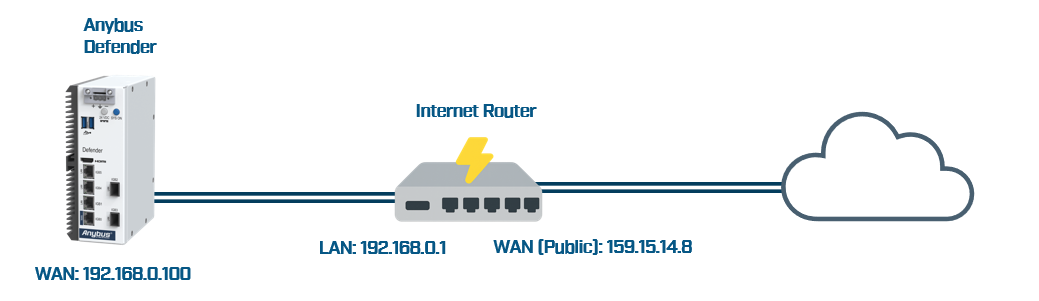
To configure the WAN interface, go to "Interfaces > WAN (igb0)" :
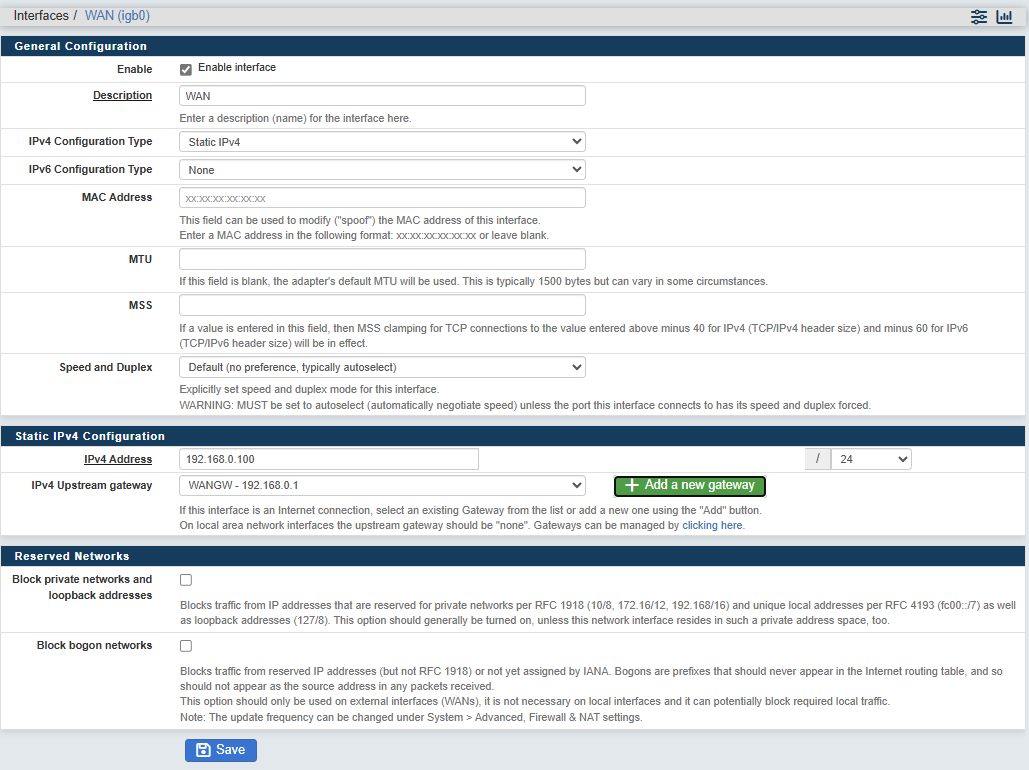
- IPv4 configuration type : Select "Static Ipv4"
- IPv4 Address: type your WAN IP address. In our example "192.168.0.100"
- IPv4 Upstream gateway, add a new gateway which is your Internet router IP address. In our example "192.168.0.1".
Also a firewall rule must be added into the Anybus defender as all the incoming traffic is blocked by default on the WAN IP interface.
For this go to "Firewall > Rules" and click 
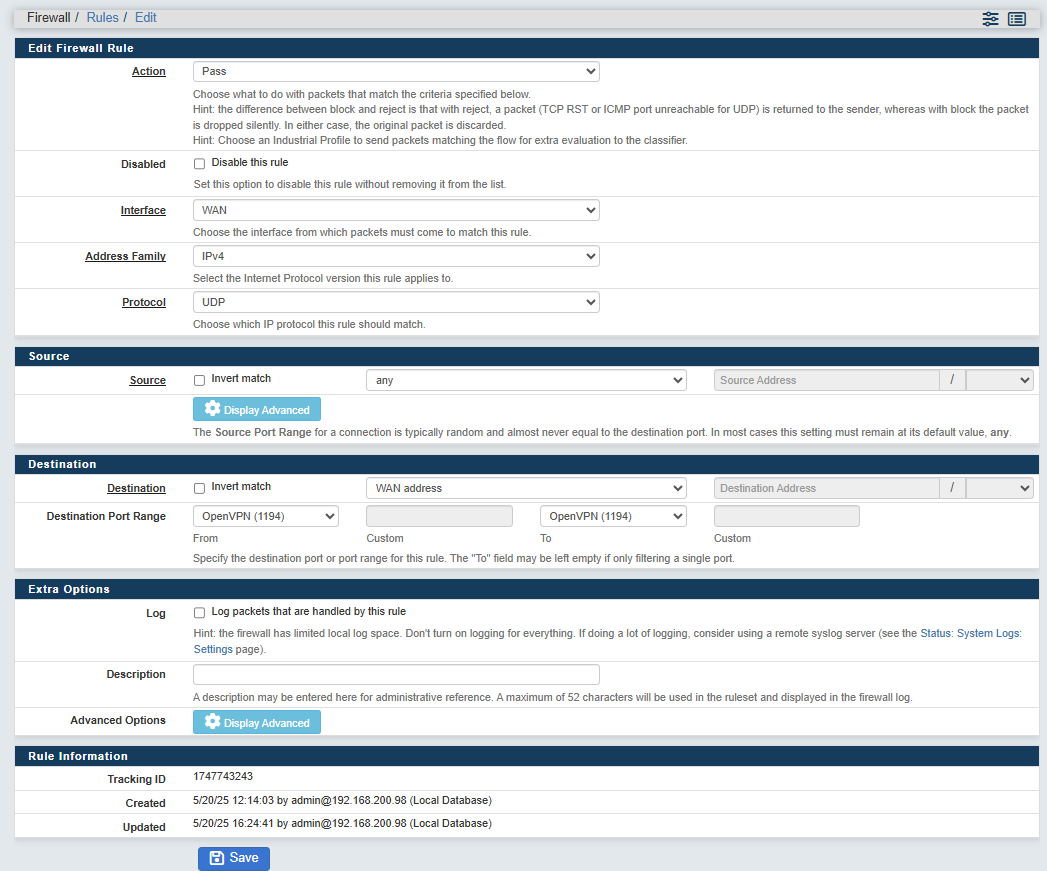
- Action: Select "Pass"
- Interface: Select "WAN"
- Protocol: Select "UDP" (This depends on your OpenVPN Server configuration)
- Source: Select "Any"
- Destination: Select "WAN address" and "OpenVPN (1194)" for "From" and "To" ports (This depends on your OpenVPN Server configuration)
OpenVPN Server
Certificates generation
First, a "Certificate Authority" certificate and a "Server" certificate are required for creating your OpenVPN Server instance.
To create these certificates go to "System > Cert. Manager "
To generate the CA certificate, go to the "CAs" tab and click  .
.
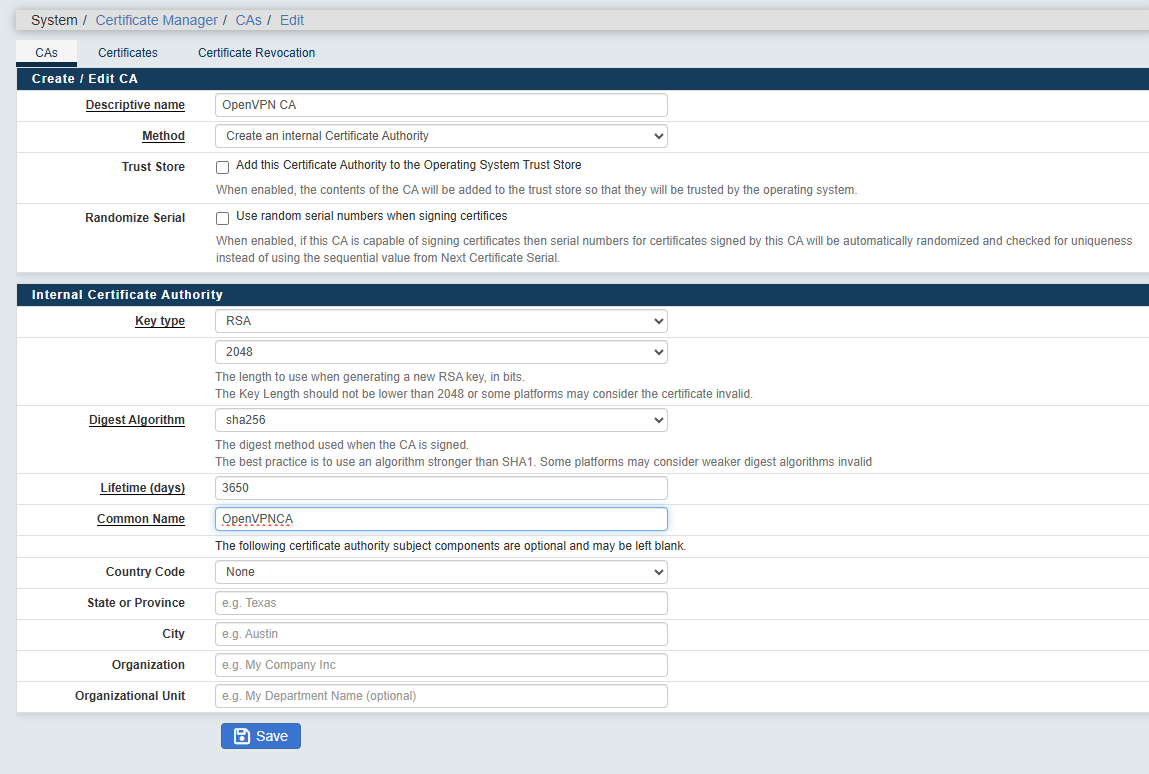
Define your CA certificate :
- Descriptive name: give a name to the CA
- Method: select “Create an internal Certificate Authority”
- Internal Certificate Authority
- Key length (bits): 2048
- Digest Algorithm: sha256
- Lifetime (days): 3650
- Common Name: OpenVPNCA
- Country Code, City, Organization: Optional info, but useful to identify the certificate
Let's generate the server certificate now. Got to the tab "Certificates" click 
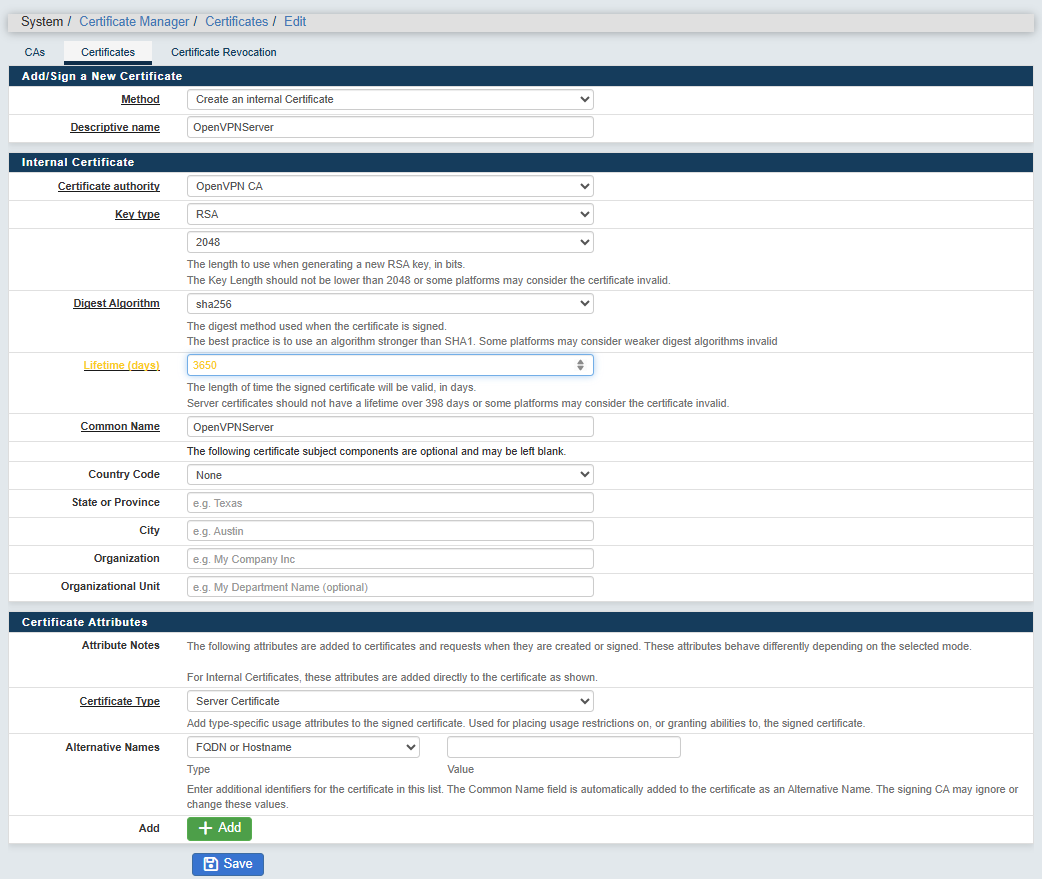
Define your Server certificate :
- Give a "Descriptive name" and a "Common Name". Here, "OpenVPNServer" has been used for both.
- Select the CA Certificate you have just created for the Certificate authority (Here "OpenVPN CA").
- Key type : RSA 2048
- Digest Algorithm: sha256
- Lifetime (days): 3650
- Common Name: here we will use "OpenVPNServer"
- Country Code, City, Organization: Optional info, but useful to identify the certificate
- Certificate Type : Server Certificate
VPN Server Configuration
Go to "VPN > OpenVPN".
In the "Servers" tab, click  .
.
General Information
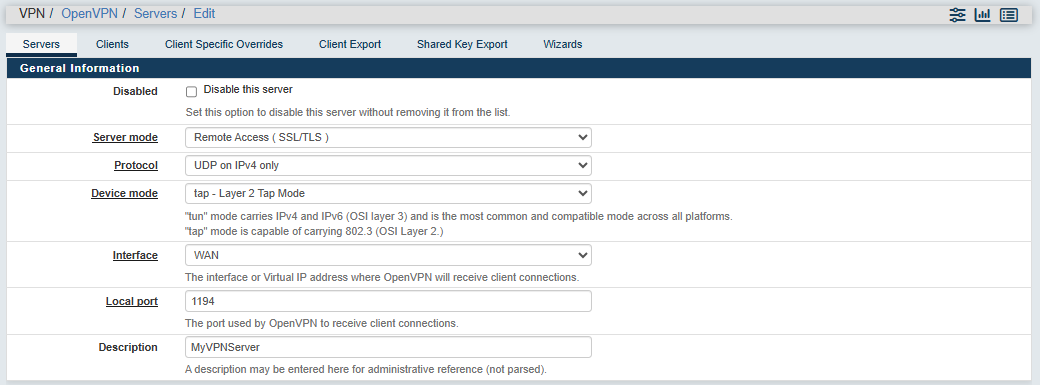
- Server mode: select “Remote Access (SSL/TLS)”
- Protocol: select “UDP on IPV4 only”
- Device mode: select “tap – Layer 2 Tap Mode”
- Interface: select “WAN”
- Local port: 1194
- Description: MyVPNServer (give a name to identify this instance of OpenVPN)
Cryptographic Settings
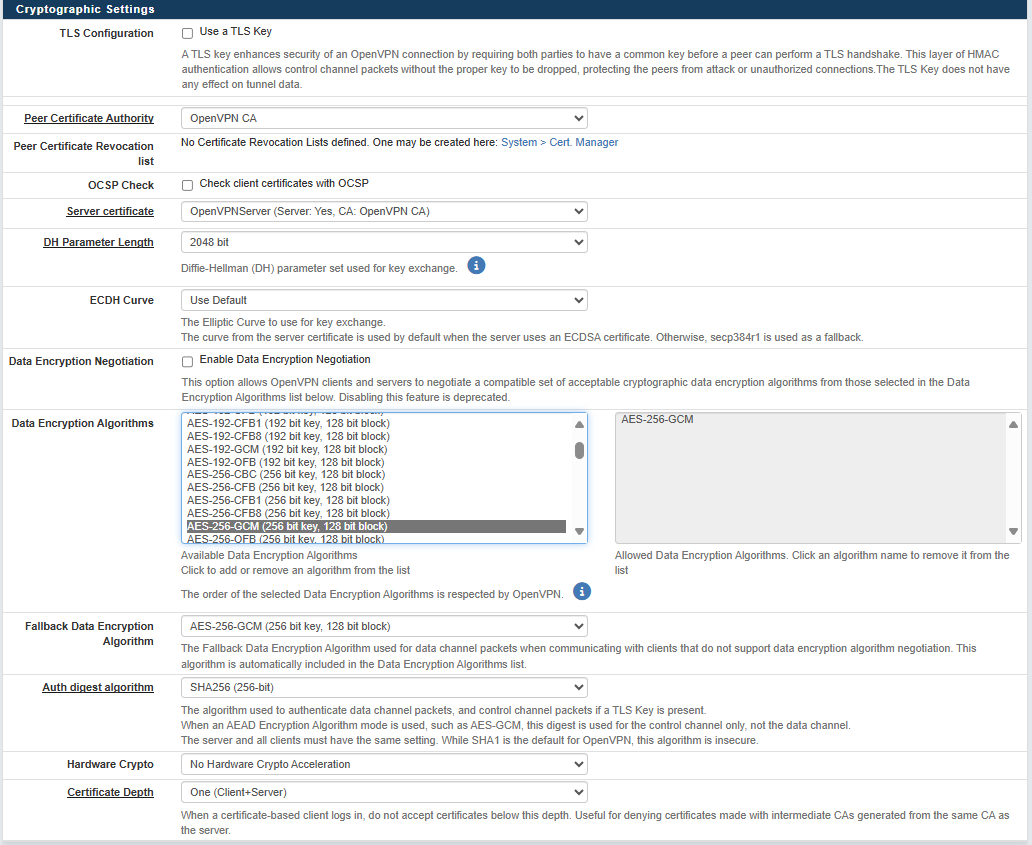
- TLS Configuration: Uncheck the “use a TLS Key” option
- Peer Certificate Authority: Select your CA certificate "OpenVPN CA"
- Server certificate: Select the Server certificate created above. Here "OpenVPNServer".
- Data Encryption Negotiation: Disable it
- Data Encryption Algorithms: Only allow "AES-256-GCM". AES-256-GCM is today the most secure symetric algorithm.
- Fallback Data Encryption Algorithm: Select "AES-256-GCM"
- Auth digest algorithm: SHA256
Tunnel Settings
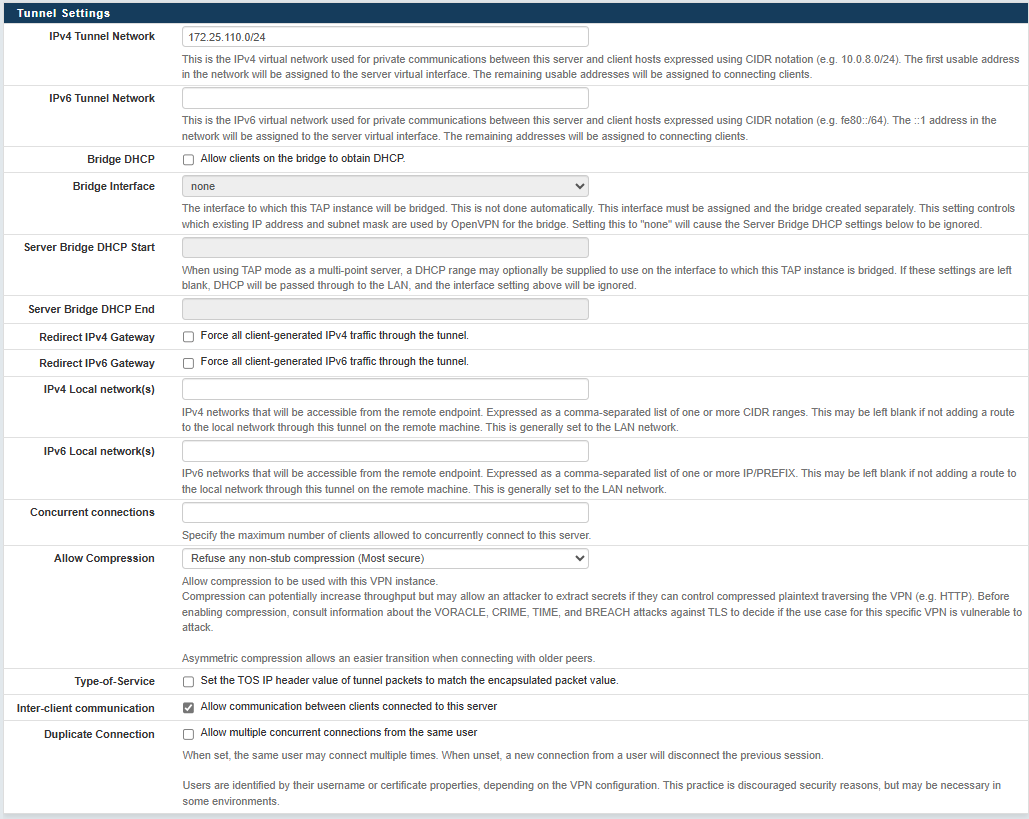
- IPv4 Tunnel Network: Specify the IP network of your VPN Network. IP addresses from this IP network will be assigned to your VPN Clients (Ewon Device and Computer). Use a network outside of any LAN or WAN networks used in your architecture.
Recommendation: Use a 172.25.x.0 network as this one is almost never used in local networks.
- Inter-client communication: Check this option. This option allows all your VPN clients (Ewon Devices and computers to connect to each other.)
For the rest of settings, you can keep them as default.
VPN Client Configuration
For each Ewon device or computer you want to connect to the OpenVPN Server, you need to create a user and a user certificate.
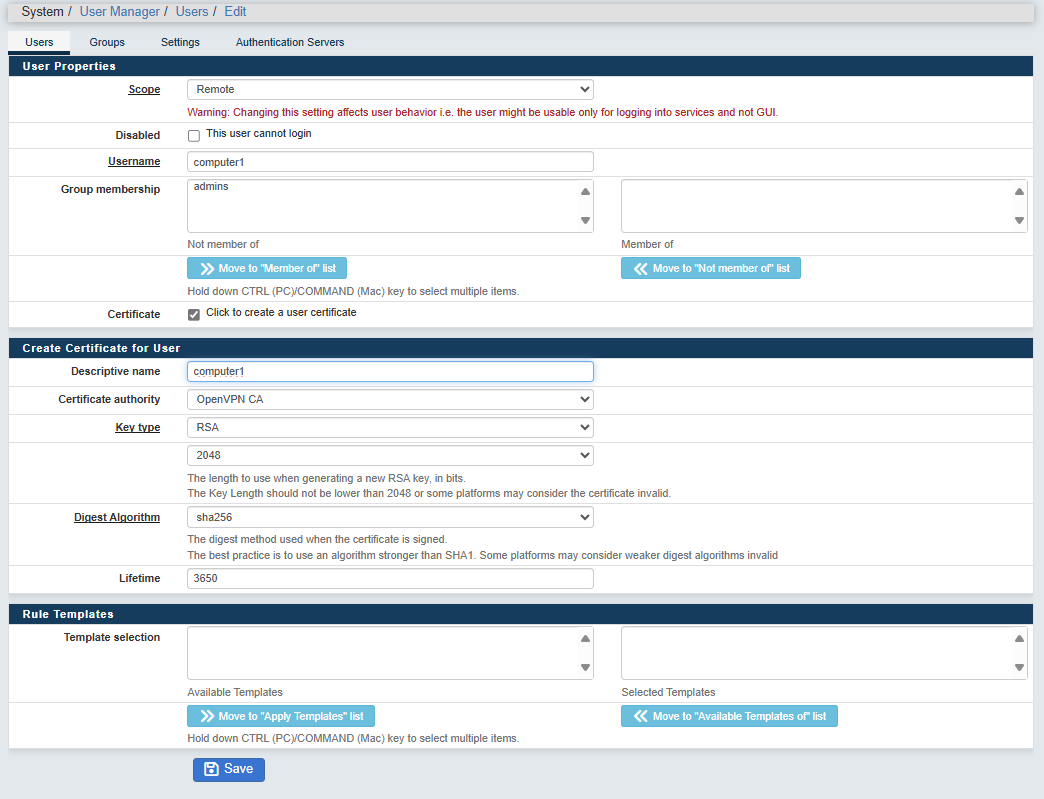
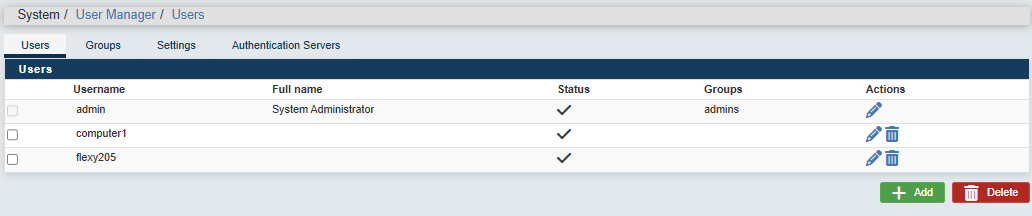
To do so, go to "System > User manager" and click 
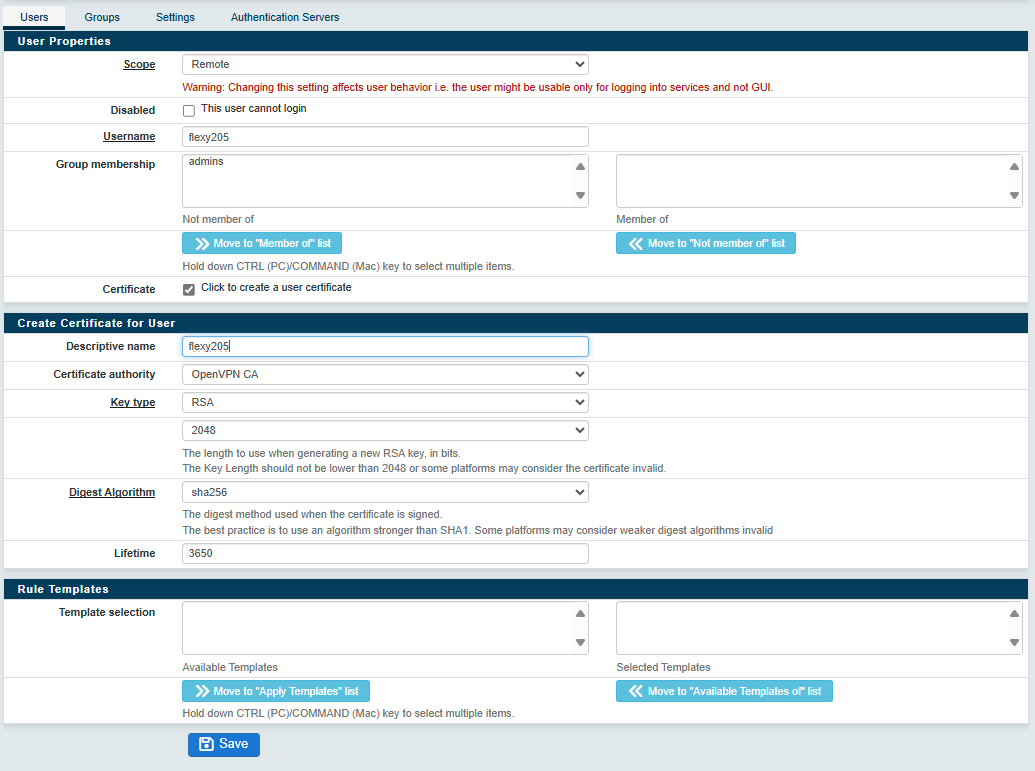
- Scope: Remote
- Username: type a unique name. Use small character only.
- Password: There might be a bug in the Anybus Defender interface here. Select "Local" as Scope, set the password and select "Remote" again. The password is useless but it will refuse to create the user if the password is not set.
- Certificate: Select "Click to create a user certificate"
- Descriptive name: easier to use the same name as the username.
- Key type: RSA
- Digest Algorithm: sha256
- Lifetime: 3650 (for 10 years)
Ewon Flexy/Cosy configuration
To configure the VPN Client connection in the Ewon Flexy or Cosy, follow the next steps :
- Go to "VPN > OpenVPN"
- Click "Client Export"
- At the bottom you can down the OpenVPN Client config file by clicking "Most Clients"

- Upload the config file as it is to the Ewon device usr/ partition by FTP.
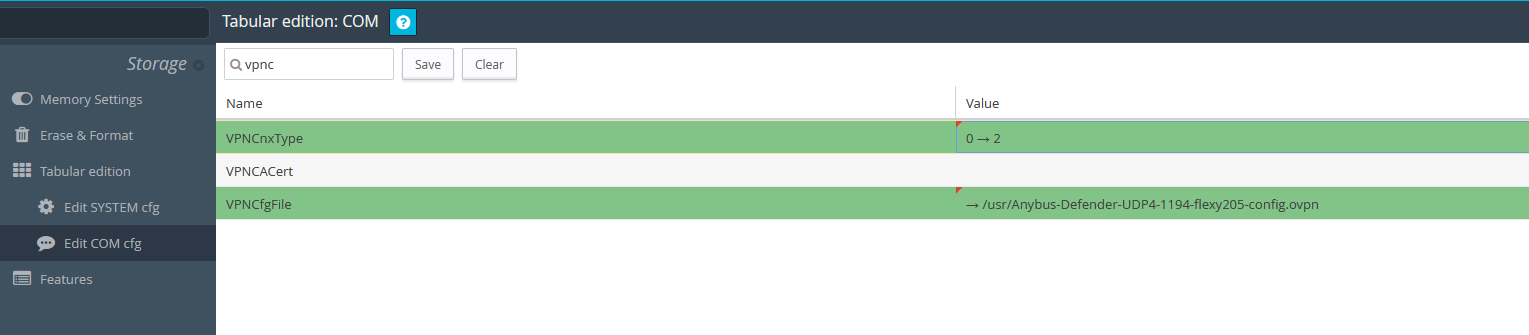
- Set the parameters VPNCnxType to 2 and VPNCfgFile to "/usr/<ConfigFileName>.ovpn"
(assuming the Ewon device has default communication settings. In case of doubts, perform a factory reset of the device) and save.
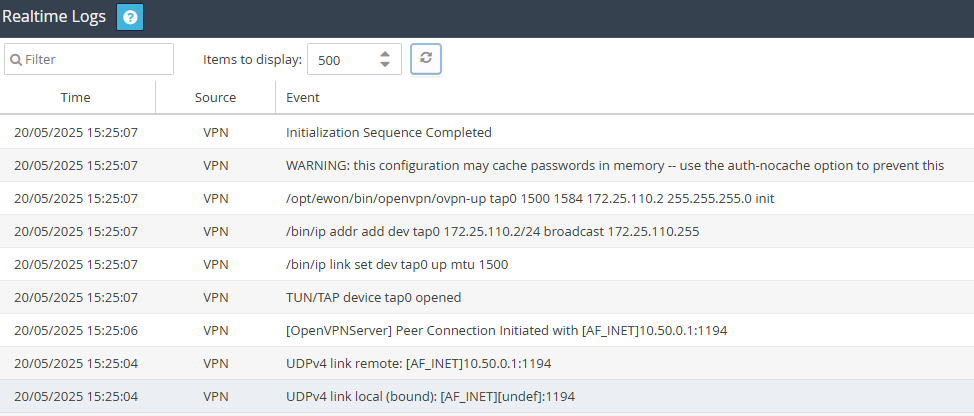
- Check in the real time logs if the connection is successful :
Computer configuration
- Follow the same steps as for an Ewon device :
- In the Client Export menu, select "Current Windows Installer > 64 bits" (depending on your system).

- Download it on your VPN Client computer and run it :
- You should then have a new open VPN tray component available in your task bar :

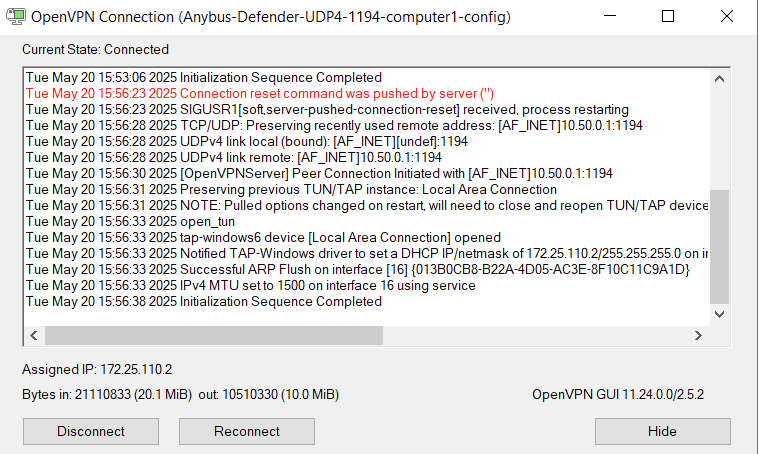
- By clicking it you should see that the VPN client connection is established :
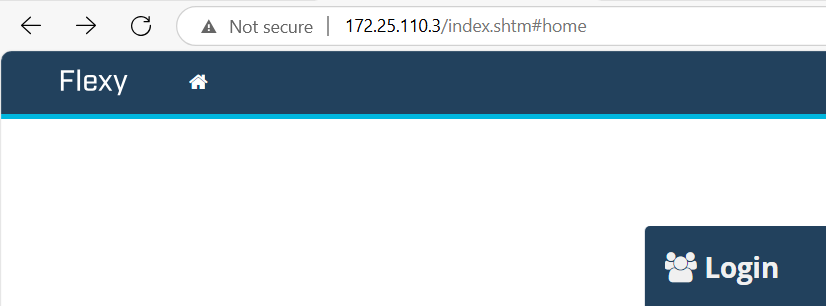
- You can then connect to the remote Ewon device by using its VPN IP address :
- You can access the Ewon LAN network by adding a route manually on the computer :
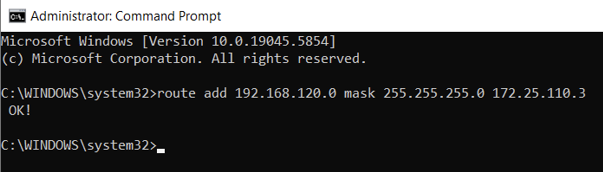
and the Ewon LAN IP address should be accessible :
If you want to connect the LAN devices connected to the Ewon LAN port, you should make sure the NATonLAN (Plug&Route) is enabled in the Ewon device.
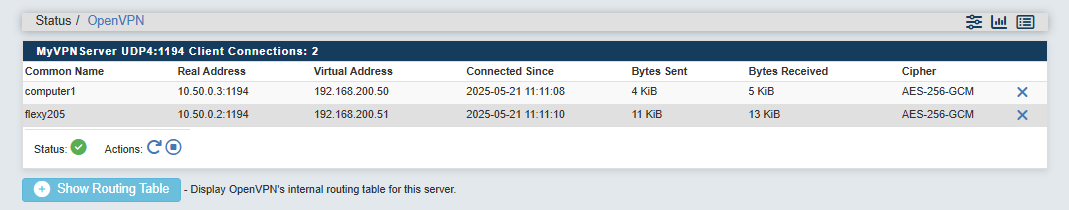
Monitor the VPN clients connected to your Anybus Defender OpenVPN Server.
To so, go to "Status > OpenVPN"
ADDITIONAL INFO
.
.