Abstract: Response for ICS-CERT Security Notice
This document will help explain the necessary steps to resolve security issues found as a result of loading new firmware.
CVSS v3 Base Vulnerability Score:10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C)
|
Severity
|
Base Score Range
|
|
None
|
0.0
|
|
Low
|
0.1-3.9
|
|
Medium
|
4.0-6.9
|
|
High
|
7.0-8.9
|
|
Critical
|
9.0-10.0
|
Products:
ST-IPm-8460
Versions Affected:
- Firmware: 7.0.101 or greater
- Tool Kit 5.0.100 or greater
Revision Information: 28 April 2022
Vulnerability: Sixnet Universal Protocol UDP/IP Undocumented Function Codes
The universal protocol implementation in Sixnet UDR UDP/IP allows remote attackers to execute arbitrary code; read, modify, or create files; or obtain file metadata via function opcodes.
Mitigation - Enable User Authentication:
- Using the Toolkit program, go to Configuration>>Configuration Station/Module >> Configure Users.
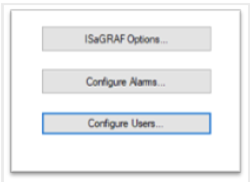
- Check the “Enable user authentication” check box.
- Remove all permissions from the ‘anonymous’ user.
- Click the “Add User…”, add user name and password, then set permissions for the user.
- After the configuration is loaded to the RTU user authentication is enabled in the RTU.
Vulnerability: Sixnet Universal Protocol TCP/IP Undocumented Function Codes
The Universal Protocol implementation in Sixnet UDR TCP/IP allows remote attackers to execute arbitrary code; read, modify, or create files; or obtain file metadata via function opcodes.
Mitigation – Disable Sixnet UDR TCP/IP:
- Connect to RTU Port via Serial port or the Ethernet Port.
- Go to Configure>Configure Station\Module.
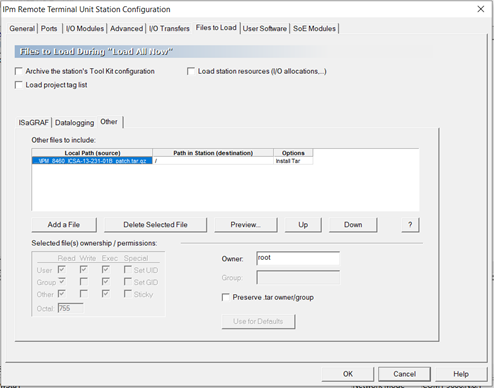
- Go to the “Files to Load” tab.
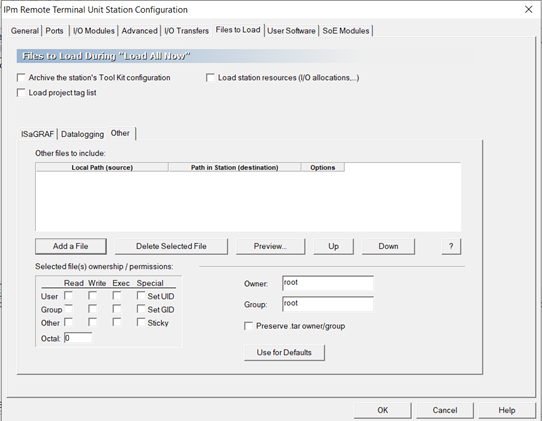
- Select “Add a File.”
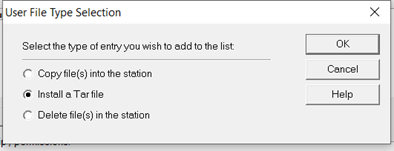
- Select “Install a Tar File” and click OK.
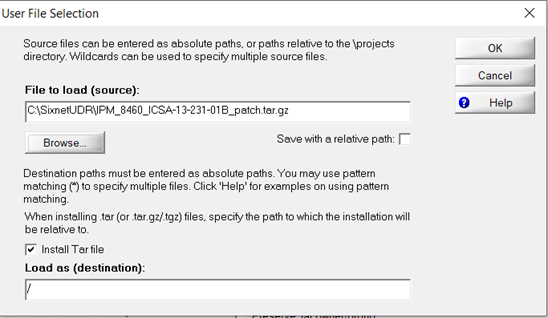
- Select the downloaded “IPm_8460_ICSA-13-231-01B_pathc.tar.gz.” Check the “Install Tar file” checkbox. Load as destination must be the root directory. Click OK.
- The “Files to Load” tab has the patch listed. Click OK.
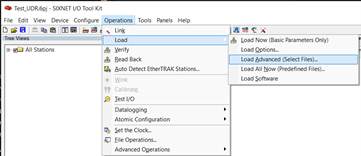
- Next, load the patch to the RTU. Go to Operations>Load>Load Advanced. Select the user file and click load
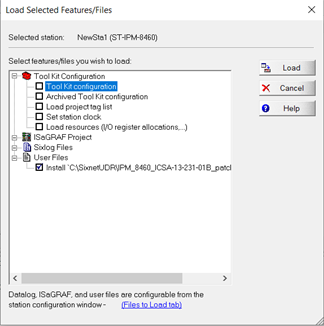
- Once loaded cycle power to the system. This must be done every time the firmware is loaded to the RTU.
Mitigation – Enable iptables Rules to block certain TCP/IP traffic:
- In the Sixnet I/O Tool Kit go to Configuration>Configuration Station/Module>”Ports” tab>Security.
- Select the “Load the this file with each station load” radio button to load a custom rc.firewall configuration file. The rules below will allow all other traffic except Sixnet UDR over TCP/IP.Please Note: Two rules that are added in by default were removed because they will block alltraffic going into the interface.
# Drop everything coming in
iptables -P INPUT DROP
# Drop everything in FORWARD chain
iptables -P FORWARD DROP
Remove these rules from the default rc.firewall file
Add one DROP rule which will drop all TCP/IP packet coming on UDR port 1594
#!/bin/sh
# Initialization
insmodip_tables
insmodiptable_filter
insmodip_conntrack
insmodiptable_nat
# Flush INPUT chain
iptables -F INPUT
# Flush OUTPUT chain
iptables -F OUTPUT
# Flush FORWARD chain
iptables -F FORWARD
# Zero counters
iptables -Z
# Drop everything coming in
# Drop everything in FORWARD chain
# Accept everything going out
iptables -P OUTPUT ACCEPT
# Allow local traffic
# Block all TCP traffic coming on port 1594
iptables -A INPUT -p tcp --dport 1594 -j DROP
Example rc.firewall rules blocking Sixnet UDR TCP/IP
- ICS-CERT also encourages asset owners to take additional defensive measures to protect against this and other cybersecurity risks.
- Minimize network exposure for all control system devices. Critical devices should not directly face the Internet.
- Locate control system networks and remote devices behind firewalls, and isolate them from the business network.
- When remote access is required, use secure methods, such as Virtual Private Networks (VPNs), recognizing that VPN is only as secure as the connected devices.